You 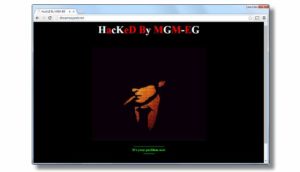 wake up and prepare for your day’s work, and suddenly things aren’t going as planned. In our case, the date was Monday 12/16, and it was just a Website Hack, but there are some important lessons to be learned and shared.
wake up and prepare for your day’s work, and suddenly things aren’t going as planned. In our case, the date was Monday 12/16, and it was just a Website Hack, but there are some important lessons to be learned and shared.
Our site, like countless others on the internet is based on WordPress. WordPress is powering over 23% of websites, worldwide. While there are other solutions for websites, in the world of Content Management Systems (CMS), WordPress owns 61% of the market with the next closest at only 7.7%. The benefits of using a popular platform are many, including; functionality, broad support, easy learning, and low cost. WordPress is also an open source solution, with a large community of contributors delivering features and functions for just about anything you would ever want to do. That’s a double edged sword – while there’s a huge community delivering new functionality, not all are following good software development practices.
It’s definitely a buyer-beware world. Building a secure site with a popular platform like WordPress means keeping current and selecting add-ons carefully. Our likely vulnerability? A simple Slider (pretty graphics) Plug-In. It appears that ours was one of over 100,000 sites that were compromised. In this fast paced world of technology, it more likely when, than if, but there are still actions to take that will reduce your risk. The rules for selecting Plug-Ins aren’t unlike rules you should use in selecting automation products; 1) pick reputable sources, 2) make sure they are proven, widely used and recommended – look for references, 3) choose only those that you really need in order to minimize your exposure and avoid customizing your solution. Even with these precautions, things can go wrong. No complex product is perfect, from the operating system, to a software application or even the integration applied to craft your unique solution.
Here are our Guidelines to minimize your risk:
- Select mainstream and popular solutions.
- Minimize technology integration. If the product doesn’t deliver what you need, you are better off finding a product that does, rather than increasing your risk through integration to fill gaps. Integration will limit your ability to upgrade and will complicate acceptance testing.
- Use proven products – ideally security tested products. While no product is perfect, having passed some level of testing is a major step in the right direction.
- Follow good application practices. Keep up with all available patches. Automate backups. Leverage firewalls where possible to regulate access. Use Strong Passwords.
With respect to automation products and security, ICS-CERT (Industrial Control Systems Cyber Emergency Response Team), https://ics-cert.us-cert.gov offers a database of tested products. Choosing products that have been tested is one major step toward creating a lower risk automation environment.
Developing corporate dashboards, compliance and performance reports?
Dream Report is a dashboard and report solution for industry that meets all the requirements listed above. It is the recommended solution of leading automation vendors in industry including Schneider Electric, GE Intelligent Platforms, ARC Informatique, Eurotherm, Wonderware, Yokogawa, Indusoft, Inductive Automation, Mitsubishi, Siemens, B-Scada, Semaphore, Trihedral, among others.
Dream Report is a “One and Done” dashboard and reporting solution. It delivers data source connectivity, statistics, formatting, delivery, archiving and web portal interaction, all in one comprehensive solution. No other system integration is required.
Dream Report is a tested and field proven solution. Please review our ICS-CERT listing.
References:
http://w3techs.com/technologies/overview/content_management/all
